
MISC_内存取证_Volatility使用
MISC 内存取证 Volatility使用¡
从零开始的内存取证训练,工具为Volatility,面向CTF-MISC做的训练记录,同时会记录Volaitlity的使用,Volatility的版本可能会根据不同的题目更换
Memslab 入门
0x01 lab0 Never Too Late Mister
题目来源于:[MemLabs/Lab 0 at master · stuxnet999/MemLabs (github.com)](https://github.com/stuxnet999/MemLabs/tree/master/Lab 0)
题目描述:
My friend John is an “environmental” activist and a humanitarian. He hated the ideology of Thanos from the Avengers: Infinity War. He sucks at programming. He used too many variables while writing any program. One day, John gave me a memory dump and asked me to find out what he was doing while he took the dump. Can you figure it out for me?
加粗信息为可能很重要的信息,对于取证来说,题目描述和背景是很重要的
- 工具:
Volatility2 - **拿到镜像的第一步:
imageinfo**,在Suggested Profiles中看见系统信息,选择Win7SP1x86进行下一步分析
1 | vol.py -f Challenge.raw imageinfo |
- 如果没有特别的思路,先
pslist查看一下进程
1 | vol.py -f Challenge.raw --profile=Win7SP1x86 pslist |
如果发现了cmd.exe的话,就cmdline、cmdscan、consoles三件套查看一下
- 在
cmdscan中发现运行了一个python文件
1 | vol.py -f Challenge.raw --profile=Win7SP1x86 cmdscan |
cmdscan不能看见输出,转为consoles
consoles查看,发现了python的输出为一串hex335d366f5d6031767631707f
1 | vol.py -f Challenge.raw --profile=Win7SP1x86 consoles |
- 丢给cyberchef,
from hex,发现是乱码 - 回想到题目信息中的environment,猜测需要查看环境变量,于是使用
envars查看环境变量,里面果然发现了Thoans,xor and password
1 | vol.py -f Challenge.raw --profile=Win7SP1x86 envars |
- 再次丢给
cyberchef,利用magic查异或,拿到了类似1_4m_b3tt3r}

- 还剩一个password没用,提到password就必须要提到
hashdump,lsadump,以及神器mimikatz,mimikatz需要自行安装,这里mimikatz秒了
1 | vol.py -f Challenge.raw --profile=Win7SP1x86 mimikatz |
- 最后的flag:
flag{you_are_good_but_1_4m_b3tt3r}
0x02 lab1 Beginner’s Luck
- 题目来源于:[MemLabs/Lab 1 at master · stuxnet999/MemLabs (github.com)](https://github.com/stuxnet999/MemLabs/tree/master/Lab 1)
- 题目描述:
My sister’s computer crashed. We were very fortunate to recover this memory dump. Your job is get all her important files from the system. From what we remember, we suddenly saw a black window pop up with some thing being executed. When the crash happened, she was trying to draw something. Thats all we remember from the time of crash.
Note: This challenge is composed of 3 flags.
工具:Volatility2
从题目描述出发,我把关键的部分都标记了:
Important files意味着filescan和dumpfiles的使用a black window pop up应该是cmd.exe,那么在pslist里肯定可以看见draw something应该是mspaint.exe,通过pslist查看
从
pslist入手,看见了几个有趣的进程cmd.exe,WinRAR.exe,conhost.exe,mspaint.exe验证了我们的猜想
1 | vol.py -f MemoryDump_Lab1.raw --profile=Win7SP1x64 pslist |
- 从cmd和conhost开始:
cmdline,consoles查看,在consoles中我们看见了敏感的数据Zmxh
1 | vol.py -f MemoryDump_Lab1.raw --profile=Win7SP1x64 consoles |
base64解码得到flag
1 | echo "ZmxhZ3t0aDFzXzFzX3RoM18xc3Rfc3Q0ZzMhIX0="|base64 -d |
- mspaint.exe:pslist查看进程号+memdump转储+改后缀为data+GIMP+翻转,
flag{Good_BoY_good_girl}

- WinRAR.exe:
filescan|grep -i rar,可以看见有个Important.rar和题目描述的important files也能对应起来
1 | vol.py -f MemoryDump_Lab1.raw --profile=Win7SP1x64 filescan|grep -i rar |
或者因为有cmd.exe,在cmdline中查看
1 | vol.py -f MemoryDump_Lab1.raw --profile=Win7SP1x64 cmdline |grep -i WinRAR |
- 转储下来,
mv指令修改文件以及文件扩展名,unrar e important.rar可以看见
1 | unrar e download.rar |
Archive comment: Password is NTLM hash(in uppercase) of Alissa’s account passwd.
- hashdump查看passwd的hash
1 | vol.py -f MemoryDump_Lab1.raw --profile=Win7SP1x64 hashdump |
所以passwd就是F4FF64C8BAAC57D22F22EDC681055BA6
- 成功看见flag3.png
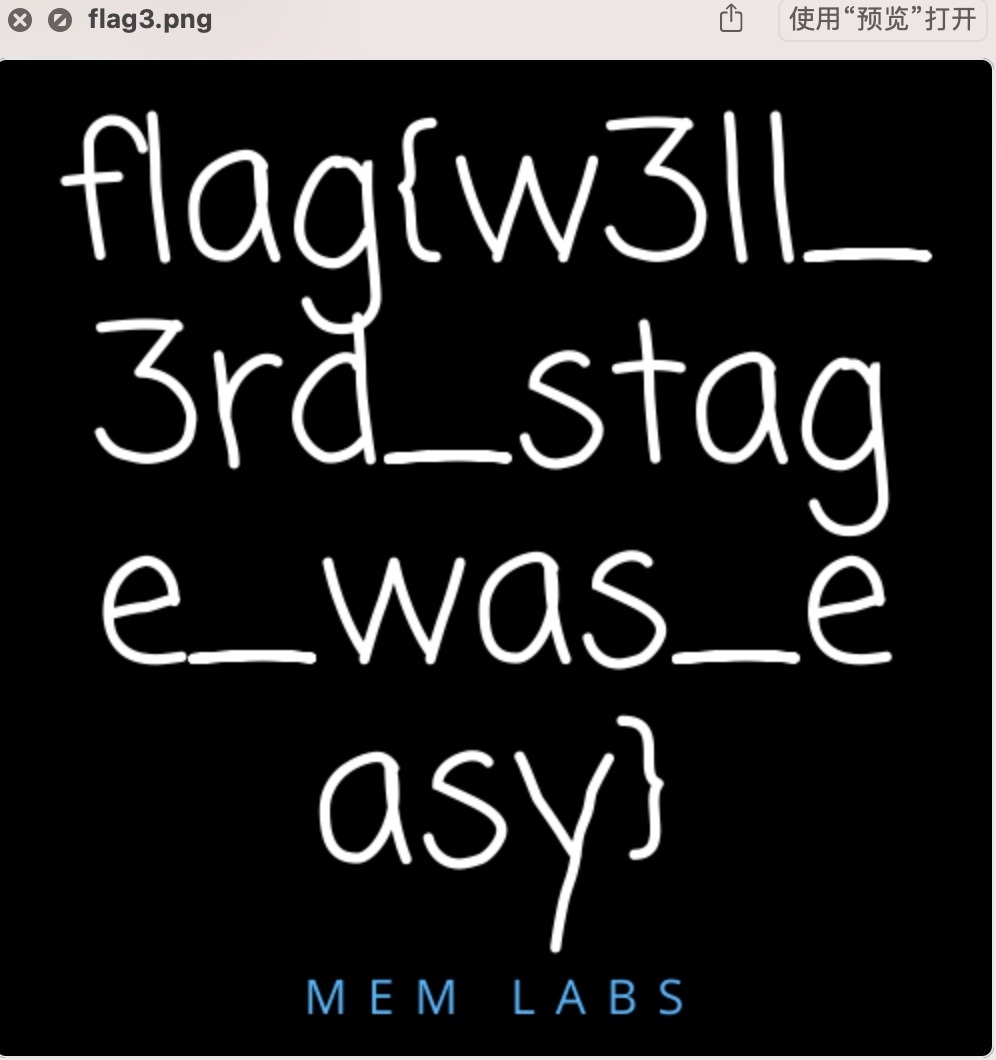
0x03 lab2 A New World
- 题目描述:
One of the clients of our company, lost the access to his system due to an unknown error. He is supposedly a very popular “environmental” activist. As a part of the investigation, he told us that his go to applications are browsers, his password managers etc. We hope that you can dig into this memory dump and find his important stuff and give it back to us.
Note: This challenge is composed of 3 flags.
根据题目描述
environmental activist-> envars- browsers需要根据pslist里显示的正在使用的浏览器,针对性的提取history
- password managers也需要根据进程,针对性的利用
那么第一步就是
envars
1 | vol.py -f MemoryDump_Lab2.raw --profile=Win7SP1x64 envars |
1 | flag{w3lc0m3_T0_$T4g3_!_Of_L4B_2} |
pslist查看,发现有chrome和KeePass
1 | vol.py -f MemoryDump_Lab2.raw --profile=Win7SP1x64 pslist |
- KeePass将密码存储在带有扩展程序
".kdbx"的数据库中,并使用主密码进行查找。于是先filescan查找kdbx,找到一个Hidden.kdbx,dumpfiles保存下来,修改后缀;但我们还缺少密码,filescan|grep -i password
1 | 0x000000003fce1c70 1 0 R--r-d \Device\HarddiskVolume2\Users\Alissa Simpson\Pictures\Password.png |
- dumpfiles后,修改后缀,打开图片发现png中存了password:
P4SSw0rd_123,打开KeePass,输入密码,导入,看见了flag字段

1 | flag{w0w_th1s_1s_Th3_SeC0nD_ST4g3_!!} |
- 查看chromehistory需要特定的插件,来源于:Volaitilty-Plugins
1 | vol.py -f MemoryDump_Lab2.raw --profile=Win7SP1x64 chromehistory |
拿到一个mega链接:https://mega.nz/#F!TrgSQQTS!H0ZrUzF0B-ZKNM3y9E76lg ,访问可以下载一个Important.zip
1 | unzip Importand.zip |
Password is SHA1(stage-3-FLAG) from Lab-1. Password is in lowercase


1 | flag{oK_St4g3_3_is_DoNE!!} |
0x04 lab3 The Evil’s Den
- 题目描述:
A malicious script encrypted a very secret piece of information I had on my system. Can you recover the information for me please?
Note-1: This challenge is composed of only 1 flag. The flag split into 2 parts.
Note-2: You’ll need the first half of the flag to get the second.
Need: Steghide
1 | vol.py -f MemoryDump_Lab3.raw --profile=Win7SP1x86 filescan|grep Desktop |
1 | #evilscript.py.py |
1 | #vip.txt |
与3异或然后base64,简单逻辑,拿cyberchef跑出结果是inctf{0n3_h4lf
根据提示,需要用到前半段,猜测前半段flag是加密的密码,由此得到后半段
1 | steghide extract -sf suspision1.jpeg |
1 | inctf{0n3_h4lf_1s_n0t_3n0ugh} |
0x05 lab4 Obsession
- 题目描述
My system was recently compromised. The Hacker stole a lot of information but he also deleted a very important file of mine. I have no idea on how to recover it. The only evidence we have, at this point of time is this memory dump. Please help me.
Note: This challenge is composed of only 1 flag.
1 | vol.py -f MemoryDump_Lab4.raw --profile=Win7SP1x64 filescan |grep Desktop |
galf.jpeg和Screenshot1.png都是兔子洞
最重要的是Important.txt,但他已经被删除了,所以dumpfiles是无法取出文件的,利用MFT表恢复文件,有两种方法:
mftparser插件- R-studio秒了
这里直接Rstudio提取,恢复important.txt
1 | cat Important.txt|tr -d '\r'|tr -d '\n' |
关于MFT表请查看:
Windows 取证之$MFT - FreeBuf网络安全行业门户
0x06 lab5 Black Tuesday
- 题目描述
We received this memory dump from our client recently. Someone accessed his system when he was not there and he found some rather strange files being accessed. Find those files and they might be useful. I quote his exact statement,
The names were not readable. They were composed of alphabets and numbers but I wasn’t able to make out what exactly it was.
Also, he noticed his most loved application that he always used crashed every time he ran it. Was it a virus?
Note-1: This challenge is composed of 3 flags. If you think 2nd flag is the end, it isn’t!! :P
Note-2: There was a small mistake when making this challenge. If you find any string which has the string “*L4B_3_D0n3*!!“ in it, please change it to “*L4B_5_D0n3*!!“ and then proceed.
Note-3: You’ll get the stage 2 flag only when you have the stage 1 flag.
1 | vol.py -f MemoryDump_Lab2.raw --profile=Win7SP1x64 iehistory |
1 | flag{!!_w3LL_d0n3_St4g3-1_0f_L4B_5_D0n3_!!} |
1 | vol.py -f MemoryDump_Lab5.raw --profile=Win7SP1x64 filescan |grep "SW1wb3J0YW50.rar" |
1 | vol.py -f MemoryDump_Lab5.raw --profile=Win7SP1x64 dumpfiles -Q 0x000000003eed56f0 -D . |
根据提示,密码应该就是flag1
1 | unrar e Important.rar |

1 | flag{W1th_th1s_$taGe_2_1s_c0mPL3T3_!!} |
procdump可以导出可执行文件
1 | vol.py -f MemoryDump_Lab5.raw --profile=Win7SP1x64 procdump -p 2724 -D . |
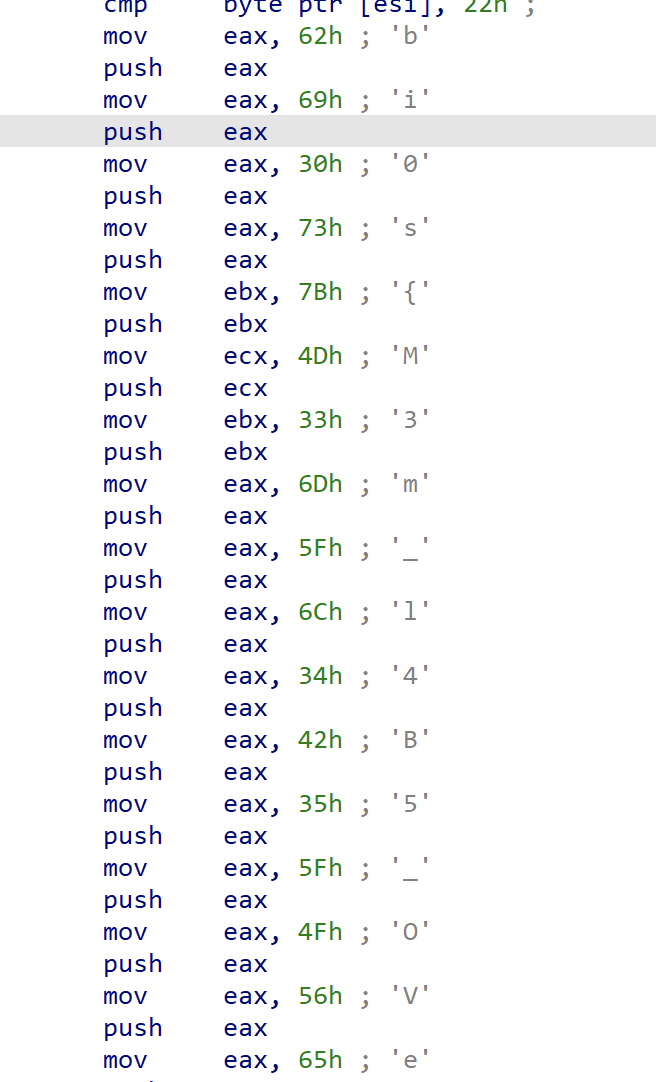
1 | bi0s{M3m_l4B5_OVeR_!} |
H&NCTF2024
wp请查看:
H&NCTF2024 - Mad1sun’s BL0G~ (madifaye.github.io)
工具为:Volatiilty2
mspaint.exe
如果在pslist中看见了mspaint.exe,可能的思路为:
- pslist查看进程号
- memdump导出进程
- 修改后缀为data
- 使用GIMP查看data文件
- 调整图像类型,多试几种(RGB、平面RGB等等),调整宽度和高度,主要调整宽度,高度可以设置在
1024左右
Volatility mftparser
如果涉及到dumpfiles无法提取文件,可以使用mftparser查看是否文件被删除,但是能通过mftparser恢复数据,复制二进制再手动转储,可以在末尾添加> 1.txt输出到txt文件中方便查看完整数据
这个功能貌似只有Volatility2有
R-Studio Network
无法提取文件,可以使用Rstudio提取
- Title: MISC_内存取证_Volatility使用
- Author: MADISUN
- Created at : 2024-05-11 20:39:17
- Updated at : 2024-05-17 17:10:06
- Link: https://redefine.ohevan.com/2024/05/11/MISC-内存取证-Volatility使用/
- License: This work is licensed under CC BY-NC-SA 4.0.